Frankly Speaking 6/22/21 - All security products suck!
Summer has officially started! I hope people are having more fun and working less. We all deserve it. I’ve found the point of diminishing returns for my work. I’m not sure if it’s a perception vs. reality issue. Anyway, I feel that I’m working less than before the pandemic, but after some analysis, I am way more productive than before the pandemic. Does the commute play a role? I know the commute takes a serious mental and even physical toll. I’m still trying to figure it out.
As many of you know, I’m trying to figure out how the future of the workplace will look like. Steven Sinofsky wrote a great tweetstorm about it. You can also find it in article form.


He explores that this remote/WFH reveals deeper issues about tech and corporations than just whether employees should work from home or not. It articulates a lot of what I’m thinking about. I would focus on Tweet 18, 27, and 28 about disruption and the types of leaders who can create disruption. Great food for thought!
LET’S BE FRANK
I’ve been ramping up my Twitter usage and trying to collect more followers, so naturally, I’ve been inspired by certain tweets (please follow me!).
The title of the newsletter says it all, which was inspired by this week.

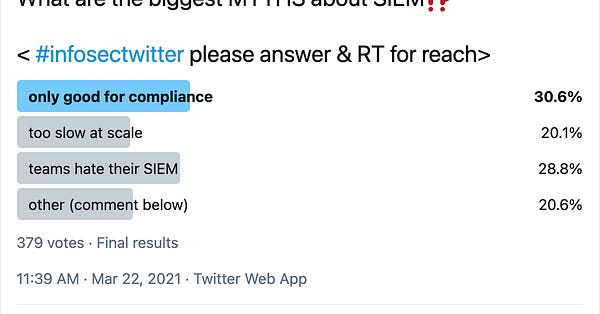
I don’t know how many times I’ve heard someone tell me “Everyone hates X. That’s why we need a new startup in this space” where X is a security tool. However, when they go out and build the product, no one is willing to displace that supposedly terrible tool, and the startup fails to get traction or has to pivot. Womps!
The tweet above summarizes this pretty well. Don’t ignore the data! Specifically, it shows that most teams don’t actually hate their SIEM. I won’t be surprised if this applied to other security products like EDR, cloud security, etc.
Follow the data, not the noise! That’s generally an important life tip, especially in security.
However, what’s up with this disconnect? Why are these “lies” so believable?
Well… at the very basic level, all security tools suck! I know that’s dramatic, but here’s the reality. The core idea of a product is that it’s useful for a broad consumer base. However, every user is different, so to create something everyone will love unconditionally is an impossible task. So, tools will always suck in some way to someone (and those voices tend to be louder).
Here are some other reasons why organizations can’t displace tools that “suck” (by no means a comprehensive list):
The tool is actually useful, but some features in it suck. However, the tool provides enough value for the organization to look past it. There are also promises from the product vendor to improve it over time.
The tool is too annoying to displace. It’s similar to 1, but the tool is too critical to risk trying something else. Either the company has invested substantially to get it to work, or it’s not clear there are obviously better products on the market, or both.
The security executive is out of touch with his/her team. The team loves the tool, but the executive doesn’t. One person hates the tool, but they aren’t the main influencer. Many people hate the tool, but the primary user loves it. The salesperson over-promised, but since the executive doesn’t actually use the tool, he/she is confused why it doesn’t work. The list goes on.
The tool sucks for its intended use case but useful for other use cases.
The tool actually sucks, but the price is so low that it’s worth the additional effort layered on top.
The tool is terrible, but it’s needed to get compliance off their back.
The executive loves getting free stuff from the company even though the product isn’t that useful.
Usually, it’s a combination of these reasons why organizations don’t displace tools they supposedly hate.
So, why is this important? Organizations are looking to displace a lot fewer products than VCs and startups believe!
This disconnect has created a market flooded with useless security products that aren’t solving real problems. I wrote about this in the past. Moreover, most products that could be displaced are in the datacenter, hence why I believe datacenter security is dead. Organizations are not looking to buy net-new products there.
So where is there opportunity in security? In solving emerging problems, e.g. cloud, cloud-native, DevOps, etc., where there isn’t an established or well-accepted solution. That’s why I’m spending so much of my time on cloud and DevOps security. It’s no surprise that the cloud security market is growing at such a strong pace without any end in sight. With that said, cloud security will grow exponentially for the next decade.
Thinking about it now, I should have made the title “All existing products in security suck, but they are hard to displace,” but that would have not been a catchy title despite being more accurate. Oh well!
Anyway, as always, please email me if you want to discuss this more or think I’m totally off base!




