Frankly Speaking, 4/2/19 -- Metadata-private messaging
A weekly(-ish) newsletter on random thoughts in tech and research. I am an investor at Dell Technologies Capital and a recovering academic. I am interested in security, blockchain, and devops.
Thanks to all for letting your friends know about the newsletter! If you're new, you can find old newsletters here. If you were forwarded this newsletter, you can subscribe here.
WEEKLY TECH THOUGHT
Users are becoming way more privacy conscious. Users query DuckDuckGo 38M times a day, up from 5M just 5 years ago. More users are complaining about Facebook's security problems, and private messaging applications like Signal are becoming more commonplace.
This week, I will discuss some cool work done by a good friend and former labmate David Lazar. For context, during our PhD, David was always the most privacy conscious person in our group, thinking that we were leaking too much data to big tech companies like Google and Facebook. At the time, I, along with many others, thought that David was being a bit too conservative, but with the recent data leaks at place like Equifax, Google+, and Facebook, David was really the right amount of cautious.
This week's tech thought is about one of his anonymous communication research projects called Vuvuzela.
Say Alice wants to communicate with Bob, her oncologist, and hide this communication. Of course, she can encrypt her messages to Bob. However, this isn’t sufficient because both parties still leak metadata through other channels. For example, Alice might communicate with the White House, NSA, and NYT, and Bob might talk to insurance and pharma companies. This metadata can reveal Alice’s and Bob’s identities. Here are some relevant but scary quotes:
Metadata absolutely tells you everything about somebody’s life — Stewart Baker, former General Counsel of the NSA
We kill people based on metadata — Michael Hayden, former Director of the NSA
To solve this problem, David built Vuvuzela, a messaging system that protects the privacy of message contents and message metadata. Users communicating through Vuvuzela do not reveal who they are talking to, even in the presence of powerful nation-state adversaries.
Of course, one can also use Tor, but past research shows that Tor isn’t that secure despite being very scalable. The goal of Vuvuzela is to be both secure and scalable.

Here is an overview of Vuvuzela:
To achieve scalable privacy, they use the following techniques:
Use efficient cryptography to encrypt as much metadata as possible.
Add noise to metadata that we can’t “encrypt.”
Use differential privacy to reason about how much privacy the noise gives us.
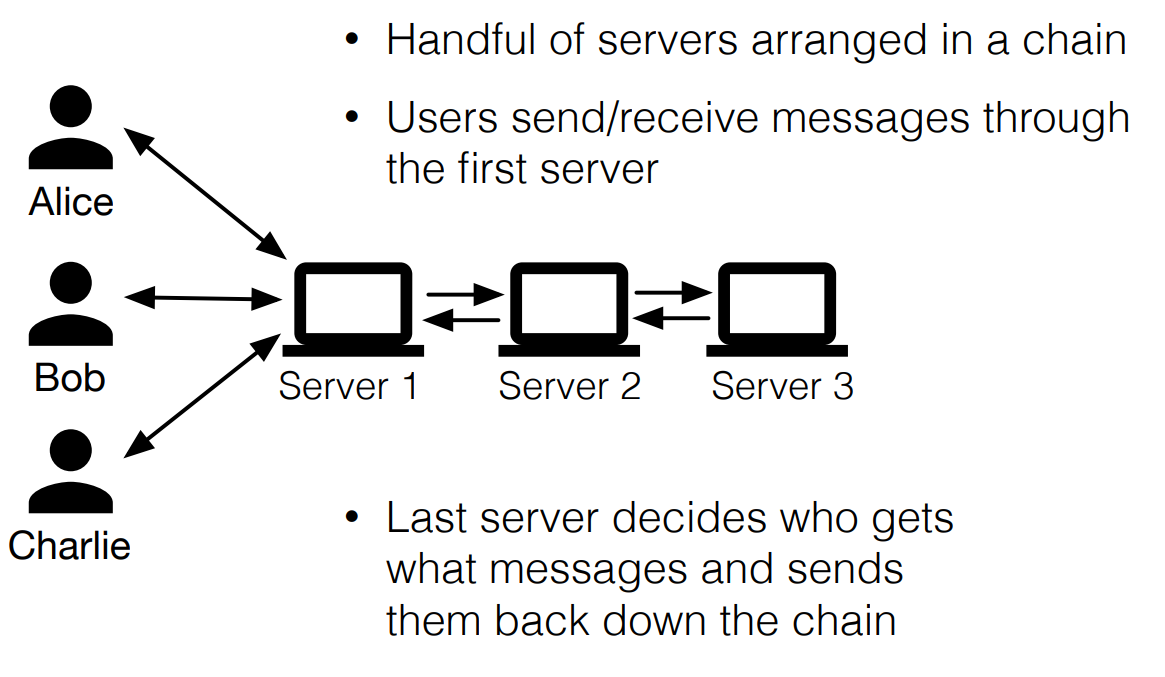
Below is a diagram of the Vuvuzela system. Alice, Bob, and Charlie are users of this system.

In Vuvuzela, users don’t communicate directly. Instead, they leave messages in “dead drops,” shown by the mailboxes on the right, intended for other users to pick up. The middle computer/servers represent a mix network that hides the origins of the messages, i.e. which user put or got a message.
However, we aren’t fully done yet. There is still some information we need to hide. The problem is that the number of items in the dead drop reveals access patterns. To solve this, Vuvuzela adds fake exchanges in the network, i.e. fake/dummy messages. To determine the amount of fake exchanges to add, they use this technique called differential privacy.
I won’t go into detail about differential privacy, but this is a good summary by Matt Green. Interesting fact is that Apple uses differential privacy to hide individual users when they collect analytics from phones and devices.
Vuvuzela uses differential privacy to determine the number of fake exchanges that need to be done on the network. The goal is to make it very difficult to guess whether a certain user has talked with another user.
Now, I’ll provide some basic performance results, but for more details, I refer you to David’s paper, where you can also learn more technical details around Vuvuzela. The system linearly scales with the number of users. It has around 37 seconds of end-to-end messages latency, and it can handle 60,000 messages per second.
David has done an interesting amount of work around anonymous communication, and I encourage that you check it out if you’re interested. As technology continues to degrade our privacy in many ways, tools to combat that trend, like anonymous communication, are definitely a necessity.
WEEKLY TWEET
This week, it's a tie between two! Both were too good to hold back.
WEEKLY FRANK THOUGHT
One of my biggest mental adjustments while switching from academic to VC is to differentiate between a technology and a product. Technologies, like AI/ML, solve technical problems. Products, like security software, are consumed by users and companies. Companies and users use and pay for products, which means they generate revenue. (Well, at least that's the goal. Consumer products work a bit different.)
Because they need to make money, companies have to build products, but sometimes an interesting technology augments the products. Technologies don't necessarily solve a business problem because well, the point of a technology is to solve a technical problem.
This might need to become a longer and more thought-through post, but I've been finding myself making this differentiation a lot as I explore the AI/ML and blockchain space. Both are technologies, which need to find applications to become a viable product. AI/ML has found interesting applications and products in security as a way to increase automation and help limited human resources focus on harder and more urgent problems. The jury is still out on blockchain, but it seems to have interesting properties, such as having no owner, being multi-writer, and decentralizing trust. However, it's not very clear what use cases these properties are useful. It seems like that any form of complication, multi-party transaction, such as supply chain or financial, would need these properties.
Anyway, products need to have users, and they need to solve problems for that user. Technologies are always a good starting point for that because it's an easy way to differentiate your product. But, not all technologies can necessarily become products.
With that said, as the tech industry matures, companies will naturally face more complicated problems, which might require more advanced products with sophisticated technologies. As a VC, I'm already seeing new technologies solve many problems more fundamentally. I find myself more often than not digging into the technical aspects of a product as the first diligence item, and we will only see more technically advanced products in the future especially for enterprise infrastructure.
FUN NEWS & LINKS
#securityvclogic
"Let's send our associates to all the booths at RSA and Blackhat, figure out which company have the least buzzwords from Kelly Shortridge's infosec bingo, and invest in those to show we really understand security."
#delltechcapital
Dell Tech Capital leads Series A funding into Cymulate, a breach and attack simulation platform.
Immuta, Dell Tech Capital company, recognized as 451 Firestarter.
Tetrate, Dell Tech Capital company, hosts first Service Mesh Day with Google and CNCF.
#research
Dorothy E. Denning writing an OG paper on how intrusion detection should work.
Dump Statistical Significance! Then, teach researchers statistics.
#tech, #security, #vclife
Good feedback to B2B founders!
Why you shouldn't (or should) be an early employee at a startup.
Sony to slash smartphone workforce.
GPS Flaw: Security Researcher don't want to travel on April 6.



