Frankly Speaking, 3/26/19 -- An Untrusted Bitcoin-Compatible Anonymous Payment Hub
A weekly(-ish) newsletter on random thoughts in tech and research. I am an investor at Dell Technologies Capital and a recovering academic. I am interested in security, blockchain, and devops.
Welcome to the second edition of Frankly Speaking! This newsletter is an ongoing experiment, so any feedback would be appreciated. Please email me at frank.y.wang@dell.com.
WEEKLY TECH THOUGHT
It's no surprise that blockchain has been all the buzz lately, but the frustrating fact is that there's very little substantive content around the hype. This week, I will be talking about a paper by Ethan Heilman and Sharon Goldberg from Boston University. Interestingly, they are now founders of Arwen (formerly known as Commonwealth Crypto), which provides protection for cross-blockchain transactions using a non-custodial trading protocol. In fact, Arwen is inspired by a previous research project that I might discuss in a separate blog.
One major feature of blockchains is the decentralization of trust. For example, Bitcoin assumes that if 51 percent of the mining power is honest, then it is secure. This paper challenges that assumption to show other avenues of attack to gain control over Bitcoin blockchain. Specifically, it attacks the Bitcoin peer-to-peer network and uses information eclipsing to subvert Bitcoin's security.
The key insight is that Bitcoin's security assurance relies on an assumption that all parties see valid blocks/transactions, but Bitcoin relies on its own peer-to-peer network to deliver its information. Consequently, if you control the peer-to-peer network, you control the information flow, and subsequently, can control the blockchain.
For some background, a Bitcoin node has 117 incoming TCP connections by default, and has a maximum of 8 outgoing TCP connections. These connections form the gossip network to propagate Bitcoin transactions and blocks. The attack targets only the Bitcoin nodes that accept incoming connections because not all nodes accept incoming connections.

What is an information eclipse attack? An information eclipse attack is an attack that gains control over a node’s access to information in the peer-to-peer network. With proper manipulation of the peer-to-peer network, an adversary can eclipse a node so that it is only communicating with malicious nodes.
What can an attacker do with an eclipse attack? It allows the attacker to launch a 51 percent attack with 40 percent mining power. Suppose the network contains 3 large mining nodes. Two control 30 percent of the mining power, and one controls 40 percent. If the attack owns the 40 percent mining power node, it can partition the other 2 miners so that they cannot build off of each other’s blocks, and can outcompete each partitioned miner. As a result, the attacker’s blockchain becomes the consensus blockchain. Another attack is the n-confirmation double spending attack. This attack is more complex and is described in more detail in the paper.
How does an attacker eclipse a node? To do this, an attacker can manipulate the node so that all its outgoing connections are to attacker IPs. This can be done simply. First, fill the node’s peer tables with attacker IPs. Then, the node restarts and loses its current outgoing connections. Finally, the node makes new connections only to the attacker IPs. The image below represents a more detailed description on how to carry out the attack.
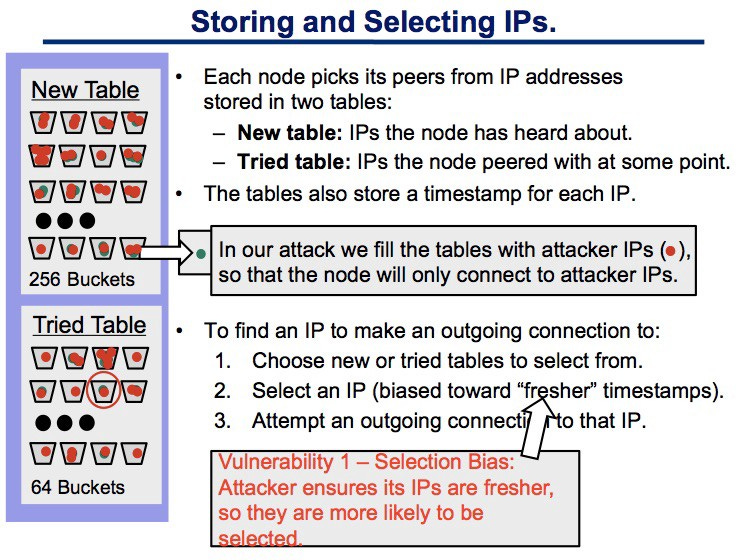
One question is how easy are restarts? The attack requires the users’ nodes to restart. However, this occurs fairly frequently because of software updates, packets of death/DoS attacks, and power/network failures. As a result, Bitcoin assumes that the uptime of the node is 100%, which seems unreasonable.
How many nodes does an attacker need? With simulations, Ethan used a botnet of 4600 IPs, 2 IPs per group, and 5 hours of time to artificially fill a node’s tried IP table successfully. This is relatively small given that Walowadac Botnet has 160,000 IPs and 25,000 groups, which shows this attack is in the realm of possibility. Then, he performed a live experiment. He used 400 IPs = 400 groups and 1 IP per group with 1 hour, and populated 57 percent of the tried table with attacker IPs.
He provides some countermeasures against this attack. To prevent the attacker ensuring its IPs are fresher so they are more likely to be selected, Bitcoin should randomly select IPs with no bias toward fresher timestamps. The attacker exploited eviction bias toward older IPs and exploited the randomness in the eviction process to improve the odds of filling tried table by running the attack multiple times. To prevent this, we deterministically map IPs to buckets and positions in buckets, evicting whatever happens to be in that position.
Another problem is that the tried table fills up very slowly and contains mostly dead IPs. To prevent this, Bitcoin should make test connections to IPs to fill tried tables faster. Finally, good IP addresses from tried table gets evicted. To prevent this, Bitcoin should test IPs in the tried table and should not evict them if they are still online.
Some of these countermeasures have been included and patched. This work demonstrates that Bitcoin’s security model, like any other security model, can be subverted through other means and "side channels."
WEEKLY TWEET

WEEKLY FRANK THOUGHT
I am very fascinated by the cost of purchased beverages, like boba tea, Starbucks coffee, etc, and consumers willingness to pay for them. The cost of making these beverages yourself is very low. For example, it costs me less than $1 to make my own latte with high quality coffee, and this includes both cost of goods and depreciation for the equipment. The same coffee is about $4-$5 at a Starbucks or SF coffee shop. Making my own Thai iced tea costs less than $0.50 where the market cost is close to $3 on average.
This means that I can easily spend 365 x $4 = $1460 on coffee alone in a year, and I used to be very willing to do this. However, I would hesitate to spend $1000 on a new iPad. In fact, wealth manager David Bach has called the latte effect, or more recently known as the avocado toast effect, which shows that small expenditures really add up. Anyway, this logic or effect seems to be the guiding point behind many subscription based services like Netflix and Spotify. On the enterprise side, Wall Street seems to be in favor of this also by valuing subscription ARR over perpetual licenses. That's a whole different conversation though.
I'm not advocating giving up lattes or avocado toasts because there are probably easier ways to save money. However, thinking about this has made me more aware of my spending and it highlights a feature of consumer spending behaviors. Similarly, when I think about company costs for our portfolio companies, especially given a potential recession, it's important to think not only about large costs (salaries), but also small recurring costs (free food, swag, etc.).
FUN NEWS & LINKS
#securityvclogic
"Security is such a reactive industry. Let's set alerts for hacks so that we can invest in a company that prevents the hack the next day."
"Security is getting so noisy with big conferences like RSA and Blackhat. A lot of VCs don't even want to touch it. If we write blog posts before and after these conferences using the right buzzwords, we'll become thought leaders."
#research
Research-focused PlanetLab was really the original cloud.
Founder of the RSA protocol, Adi Shamir, couldn't get a visa to attend the RSA conference.
Warnings of a dark side of AI in healthcare.
#tech, #security, #vclife
JPM Coin (JP Morgan's cryptocurrency) is coming out!
... while Citi scraps its plans for a coin.
Streaming video has surpassed cable.
Orchestra 1.0 for robotic process automation is released.
Defining a distinguished engineer.
Phone numbers stink as identity proof.
File Content Disclosure on Rails.



