Frankly Speaking, 7/9/19 - Controlled Functional Encryption and "Digital Transformation" frustrations
A weekly(-ish) newsletter on random thoughts in tech and research. I am an investor at Dell Technologies Capital and a recovering academic. I am interested in security, blockchain, and devops.
If you were forwarded this newsletter, you can subscribe here, and view old newsletters here.
The summer board and conference season is upon us, but I'm getting better at keeping a regular cadence with this newsletter. The last 3 months have been crazy as I've been trying to close multiple deals, which will be announced soon! So, stay tuned.
Also, I'm going to be at Blackhat in August, so email me if you want to meet up and chat.
WEEKLY TECH THOUGHT
"Crypto" has been a term that's been thrown around a lot lately. It's now come to refer to cryptocurrency. For clarity, my PhD was in crypto, short for cryptography. Anyway, the resurrection of Bitcoin and my recent interests in blockchain has caused me to think more about cryptography. When I first started my PhD, there was limited cryptography adoption, but I am now truly amazed at how often people talk about crypto (both cryptocurrencies and cryptography). It's a cryptographer's dream to see such widespread usage. Anyway, this week's post is going to be about Controlled Function Encryption.
This discussion is based on a paper by Muhammad Naveed, now a professor at USC. The motivation behind this work is to bring modern cryptographic technology to real applications.
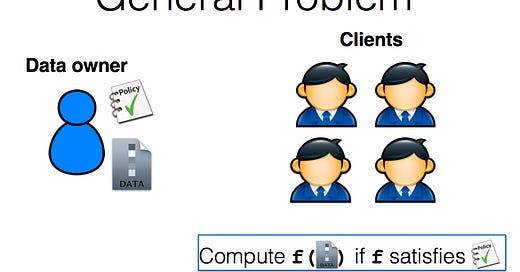
There have been numerous healthcare breaches, such as the Anthem breach. These types of hacks have affected 39 million individuals and over 1140 institutions. Similarly, in 1989, ASU researchers collected Havasupai’s DNA samples to study the Type II Diabetes, but the study was unsuccessful. However, the data was used for an anthropological study, and the results conflicted with the tribe’s beliefs about their origin. The problem is that the Havasupai tribe did not agree to have its DNA used in an anthropological study, just the diabetes study. Below is a figure of the general problem.

The goal is to create a cryptographic model that aligns well with real applications and also allows the design of practically efficient protocols. Some basic requirements of the protocol are the following:
Practically efficient for real applications
No interaction with the data owner
Data owner controls access to the data
Only the data owner sees the plaintext
Current cryptographic models don’t work and don’t meet all these requirements. Two-party computation has interaction with the data owner. Functional encryption is too slow, and there’s no good implementation. He introduces this notion of controlled functional encryption. Here is a figure outlining the protocol. If you are interested in more details on the actual construction, they can be found in his paper.

The main change between controlled functional encryption and regular functional encryption is that a different key is required and used for each decryption. This small change makes a huge difference, and it makes the problem more tractable. It also enables fine-grained access control to the data.
His research is especially interesting in the setting of genomics. He describes applications for personalized medicine and patient similarity.
Finally, he has detailed evaluations of a variety of functions in his paper to show its practicality.
I think this research is an interesting step toward making these new cryptographic models more practical. Cryptography and the public's understanding of it has come a long way in the last 5 years. Despite my annoyances around people's confusion between cryptography and cryptocurrency, I am excited that cryptography is being about more regardless of context.
LET'S BE FRANK
One term I hate is "digital transformation." It's such a vague phrase that's unnecessarily ambiguous. It's a catch all, meaningless term because it almost always requires further explanation. What's the point in having a term if you have to explain what it means all the time? Why not just start with an explanation? Why not call it an IT infrastructure transformation? Anyway, it's a term that comes up over and over again. It's interesting because our firm has always believed in the multi-cloud world, which is a company using different permutations of on-prem, private, and public clouds. You're seeing a lot more "legacy" companies move toward the public cloud, and the cloud-first companies move toward private cloud.
The reason I bring this up is that enterprise companies should focus on companies that are undergoing this "digital transformation" because chances are that they are organized using legacy stacks, which don't work on the public cloud. I'm always confused when enterprise companies focus on selling to tech companies or companies on the west coast. They are probably already organized to handle this new "enterprise" world. Companies undergoing the digital transformation really need the most help because organizationally, they are not set up to rapidly handle this change. They might still be in the waterfall format or just trying to become agile.
Anyway, the real customers are the ones that need help with their transformation, and most tech and cloud-first companies don't. If you're an enterprise company, focus on non-tech Fortune 500 and Global 2000 companies.
Next week, I'll discuss why I believe the digital transformation is a large reason for the rise of security companies and increased security spend. In short, this digital transformation has allowed companies to "reset" their security strategy.